OK, so why do I think that any linux admin should know about lsof? Well the fact is you can't deter things that you can't detect, and lsof is an excellent tool for trying to detect weird network traffic, and possibly any malware that might be on your machine. This is also a valuable part of profiling your machine so you can write rules on your firewall to block unwanted traffic.
lsof stands for "List open files." Remember, on *nix, everything is a file, including network ports. Let's just dive in by opening up a command prompt and typing lsof. You might need to run this as root or use sudo to get some results. For this first run, let's pipe the output into head so we can see the begining.
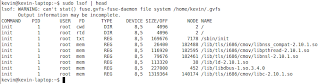
 So looking at this output you can see that there is a process called dropbox that is listening on port 17500. That same process has some connections that are in a CLOSE_WAIT state. We wont get into what that means right now, except to say that it shows that at one time my machine had a connection to those IP addresses. You can also see that I have one connection that is established, which means that it is going on right now. There is also a process called cups that is listening for connections on the ipp port.
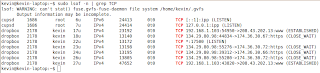
So looking at this output you can see that there is a process called dropbox that is listening on port 17500. That same process has some connections that are in a CLOSE_WAIT state. We wont get into what that means right now, except to say that it shows that at one time my machine had a connection to those IP addresses. You can also see that I have one connection that is established, which means that it is going on right now. There is also a process called cups that is listening for connections on the ipp port.The listening port is what we're interested in. We want to know everything that is listening on the network, so that we can write appropriate Access Control Lists and possibly hunt down any rogue listeners. So let's run lsof again and grep for LISTEN.

As you can see, there are only two services listening for connections. Now to demonstrate, let's create a rogue listener and see the difference. I'm going to run this command in another terminal window: nc -l 9000. Then I'll run my lsof again. I'm going to spice up this command a bit so you can see the headers too.
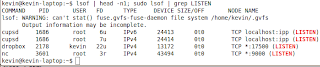
Based on the information that you've got here, you should be able to figure out what services are running each of the connections. If there are any that you can't identify, then it may be an indication of malware that you need to investigate further.

No comments:
Post a Comment